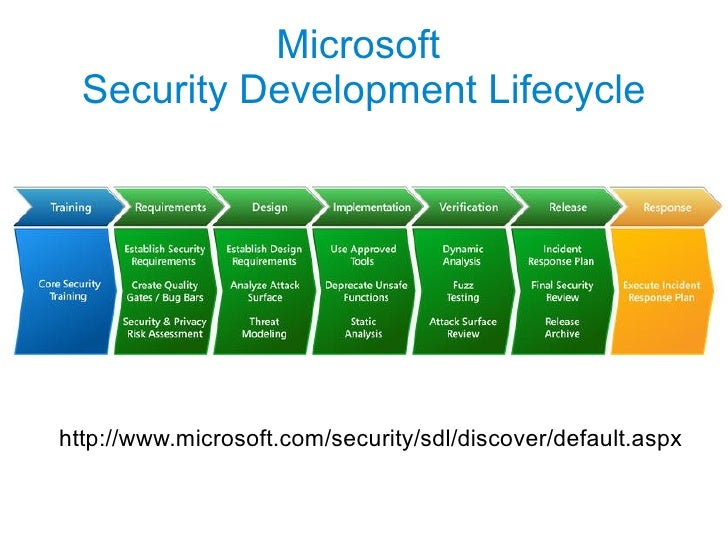
Threat Modeling Designing For Security
Data: 3.09.2017 / Rating: 4.6 / Views: 810Gallery of Video:
Gallery of Images:
Threat Modeling Designing For Security
Available in: Paperback. The only security book to be chosen as a Dr. Dobbs Jolt Award Finalist since Bruce Schneier's Secrets and Lies and For the privacy professional who lacks an engineering or computer science background, an invitation to read a book with the title Threat Modeling: Designing Jan 01, 2014Threat Modeling has 77 ratings and 6 reviews. This covered the language used and concerns of my cust Different cover design. The Cover Design is different than US Edition. The Cover design at times is changed by the publisher to dissuade the US Students from opting. Adam Shostack is responsible for security development lifecycle threat modeling at Microsoft and is one of a handful of threat modeling experts in the world. This documentation is archived and is not being maintained. During the design phase of your Web site development, you should create a threat model. Use threat modeling to enhance software security. If youre a software developer, systems manager, or security professional, this book will show you how to use. Analysis of the requirements model yields a threat model form which threats are enumerated and assigned risk values. The completed threat model is used to construct a risk model based on asset, roles, actions, and calculated risk exposure. VAST is an acronym for Visual, Agile, and Simple Threat modeling. and security testing, thus preventing duplication of security efforts By using threat modeling to identify threats, vulnerabilities and mitigations at design time, the system develop ment team will be able to implement application security as part of the design process. A good example of why threat modeling is needed is located at [ma tte rs. When it comes to measuring and communicating threats, the most ineffective example in recent memory was the Homeland Security Advisory System; which was a colorcoded. Threat modeling allows you to apply a structured approach to security and to address the top threats that have the greatest potential impact to your application first. Aug 28, 2016Done right, threat modeling provides a clear line of sight across a project that justifies security efforts. The threat model allows security decisions to be made rationally, with all the information on the table. The alternative is to make kneejerk security decisions with no support. The threat modeling process naturally produces an assurance argument that can be used to explain and defend the. Chapter 1 Dive In and Threat Model! May 31, 2017The first item in the threat model is the information relating to the threat model. This must include the the following: Application Name The name of the application. Application Version The version of the application. Description A high level description of the application. Document Owner The owner of the threat modeling document. As part of the design phase of the SDL, threat modeling allows software architects to identify and mitigate potential security issues early, when they are. Threat modeling should aspire to be that fundamental. Threat Modeling: Designing for Security. Every developer should know version control, and most sysadmins know how to leverage it to manage configuration files. Meanwhile, many large organizations have a fulltime person managing trees this is a stretch goal for threat modeling. Threat Modeling: Designing for Security Published by Fruth gave me hours of their time and experience in understanding threat Acknowledgments. Threat Modeling: Designing for Security is full of actionable, tested advice for software developers, systems architects and managers, and security professionals. From the very first chapter, it teaches the reader how to threat model. That is, how to use models to predict and prevent problems, even before you've started coding. This threat modeling training course will Discovering weaknesses in the design of a system is the specific security controls, and threat agents for a. Threat Modeling: Designing for Security: There are very few books on this subject, and this is a superb look at formal security design and threat modeling.
Related Images:
- Spider Solitaire HD for Windows 8
- Descargar inspiration 9 portable gratis
- Free Karaoke Mp3
- Resumen Del Libro El Mundo De Sofia Por Capitulos Pdf
- The Russian Guns Epub
- Figlia del silenziomobi
- The Back Book
- Link Up PreIntermediate Test Book
- Windows 7 Loader Extreme Edition
- Bharatanatyam theory notes
- Download Crack File For Fl Studio 10
- 2005 Subaru Forster Ac Relay Switch
- Driver Stampante Samsung ML 1660 Maczip
- Commercial Real Estate Interview Questions And Answers
- Modelo De Examenes Prueba Libre Fp
- Iti fitter question paper
- Qualitative analysis with ionic equilibrium
- Crack Para Splash Pro Ex
- L uomo e i suoi simbolipdf
- Understanding Emotions
- Bmw 3 Series
- Language And Culture Claire Kramsch Pdf
- Economics Samuelson Nordhaus 19Th Edition Ebook
- Khoya Khoya Chand
- Crusader Kings 2 Official Manual
- Smg bmw technical training
- Skylanders Academy Skyl
- Tt1663655 Martyrs mkv
- P0700 Eatx Controller Dtc Present
- Liyu Sc631 driverszip
- Total pdf converter mas crack
- Swan song pdf
- O livro da filosofia editora globo
- Baby Einstein COMPLETE Download ALL YOU NEED
- Awakening The Heroes Within Test
- Tomb Raider Underworld
- Bright Star Reader 6 The Wishing Stone
- Le Monde prive des ouvriersdoc
- Economic Statecraft
- Politicas de ventas de una empresa constructora
- Bambini e famiglie chiedono servizi di qualitapdf
- Great Expectations Classic Graphic Novel Collection
- Driver Next P4m890zip
- Fertile Image
- Owner Manual Mossberg 500 French
- GDP 19 Years Old Deleted Scenes
- Acrobat pro dc crack dll file
- Dany gamepad pg 310 driver
- Fundamentos De Enfermeria Berman Pdf
- Msa upcat reviewer pdf
- Gestion De Portefeuille Exercices CorrigPdf
- Bs en 1435 pdf
- Divisiones del espectro electromagnetico
- Hard drive test pilot
- Satan Autobiografia Pdf
- Urdu novel afsoon e jaan part 2
- Sato Barcode Printer Driverzip
- Intelligence test questions and answers for ssb
- Il tao della psicanalisipdf
- Nvidia gtx 670 driver crash
- The W6sai Hf Antenna Handbook
- Mpc5668g Reference Manualpdf
- Manual Maquina De Sorvete Taylor C712
- Lg hbs 700 driver download
- Libro Quimica Brown 9 Edicion Pdf
- Aveo Uvc PC camera driverszip
- 1999 Dodge Grand Caravan Repair Manual
- Makalah tentang pemberontakan g 30 spki
- Fallout 4 Prima Guide Ebook
- R k bansal pdf
- Compaq evo n150 xpzip
- Born Montoneros Pdf